Ultimate Guide to 2FA for Crypto Beginners
Learn the importance of two-factor authentication for crypto security, the best options available, and how to set it up effectively.

Two-factor authentication (2FA) is a must for securing your crypto assets. Passwords alone aren't enough - 81% of data breaches involve weak or stolen passwords. 2FA adds an extra layer of security by requiring two steps to verify your identity, such as a password and a code from an authenticator app. This makes it much harder for attackers to access your accounts, even if they steal your password.
Here’s what you need to know:
- Why 2FA Matters: Crypto transactions are irreversible. Without 2FA, you're vulnerable to SIM swapping and phishing attacks, which caused millions in losses in recent years.
- Best 2FA Options: Avoid SMS-based 2FA - it’s prone to SIM swapping. Use authenticator apps like Google Authenticator or hardware tokens like YubiKey for stronger protection.
- Setup Tips: Use an authenticator app, store backup codes securely, and test recovery options to avoid being locked out.
Quick Tip: For maximum security, combine an authenticator app for daily use with a hardware token for critical accounts. Start securing your crypto wallet today by enabling 2FA and following these simple steps.
Types of 2FA and Their Pros and Cons
When it comes to securing your crypto assets, not all two-factor authentication (2FA) methods are created equal. Let’s break down the strengths and weaknesses of three common options: SMS-based 2FA, authenticator apps, and hardware tokens.
SMS-Based 2FA
SMS-based 2FA works by sending a code to your phone via text message. While it’s easy to use and familiar to most people, it’s also the least secure.
For instance, Coinbase reported that 95% of account takeovers in November 2022 were tied to SMS-based multi-factor authentication (MFA), even though users relying on this method made up 95.65% of all account breaches. The main vulnerability? SIM swapping. In this type of attack, scammers trick your mobile carrier into transferring your phone number to their device, allowing them to intercept your 2FA codes.
Still, SMS 2FA isn’t entirely useless - it can block around 76% of automated attacks, according to Forrester. It’s a step up from having no 2FA at all but falls short when it comes to safeguarding valuable crypto assets.
Authenticator Apps
Authenticator apps like Google Authenticator, Microsoft Authenticator, and Authy offer a more secure alternative. These apps generate time-sensitive codes directly on your device, avoiding the risks associated with SMS. When setting up 2FA, you scan a QR code, which creates a shared secret between your app and the service. From there, the app generates a new six-digit code every 30 seconds.
Microsoft’s research shows these apps blocked 100% of automated bots, 99% of bulk phishing attempts, and 90% of targeted attacks. They also work offline and are immune to SIM swapping since no phone number is involved. However, losing your device without backup codes can lock you out of your accounts - a key downside to consider.
Hardware Tokens
Hardware tokens, such as YubiKey, take security to the next level by using public-key cryptography. These devices verify communication with legitimate services, making them resistant to phishing. Using one requires physical interaction with the token, like tapping it or inserting it into a device.
While hardware tokens offer the strongest protection against sophisticated attacks, they come with trade-offs. They’re less convenient, as you need to carry the device with you, and they involve an upfront cost. Additionally, not every crypto platform supports them yet, though adoption is increasing among major exchanges and wallets.
Comparison of 2FA Methods
Here’s a side-by-side look at how these methods stack up in terms of security, usability, cost, and recovery options:
| Feature | SMS-Based 2FA | Authenticator Apps | Hardware Tokens |
|---|---|---|---|
| Security | Weak; prone to SIM swapping and interception | Strong; codes generate locally and resist SIM swapping | Strongest; phishing-resistant with public-key cryptography |
| Ease of Use | Very convenient; codes sent via text | Convenient after setup; codes generate on device | Less convenient; requires carrying a physical device |
| Cost | Free | Free | Requires an upfront purchase |
| Recovery Options | Easier to recover (e.g., new SIM) | Backup codes needed; risk of lockout if lost | May need multiple tokens or backup codes |
| Offline Capability | Requires cellular network | Works offline | Works offline |
Key Takeaways
SMS 2FA should only be used as a backup option. For most users, pairing an authenticator app for everyday accounts with a hardware token for critical logins provides a solid balance of security and convenience. By understanding these options, you can make informed decisions about securing your crypto wallet effectively.
How to Set Up 2FA on Your Crypto Wallet
Securing your crypto wallet with two-factor authentication (2FA) is quick and straightforward. In just a few minutes, you can add an extra layer of security to help protect your digital assets.
What You'll Need to Get Started
To enable 2FA, you'll need a smartphone and access to your wallet's security settings. Start by downloading an authenticator app. Some popular choices include Google Authenticator, Microsoft Authenticator, Authy, or Duo - all of which are free and available on iOS and Android.
Certain platforms might also ask for additional verification, like an email address or phone number for backup purposes. If you'd prefer hardware-based 2FA, you'll need a physical security key such as YubiKey, Ledger, or Trezor.
Once you're ready, follow the steps below to set up 2FA.
Step-by-Step Guide to Enable 2FA
Although the exact process may vary slightly between platforms, the general steps are similar. For the best experience, log into your account on a desktop or laptop. Go to your account settings, typically under a menu labeled "Security", "Account Settings", or "Privacy & Security."
- Locate the two-factor authentication (2FA) section and click "Enable" or "Set Up."
- You'll see a list of 2FA options. Select "Authenticator App" rather than SMS for stronger security.
- A QR code and a text-based setup key will appear on your screen.
Next, open your chosen authenticator app and add a new account. Most apps have a "+" button or an "Add Account" option. Use your phone's camera to scan the QR code displayed on your screen. If scanning doesn't work, you can manually enter the setup key provided below the QR code.
Once the app is linked, it will generate a six-digit code that refreshes every 30 seconds. Enter the current code from the app into the verification field on the platform to confirm the setup. This step ensures your account is synced with the authenticator app, adding a crucial layer of protection to your wallet.
After verification, the platform will provide you with a set of backup codes - usually 8 to 12 alphanumeric codes. These codes are critical for account recovery if you lose access to your authenticator app.
Safeguarding Your Backup Codes
Backup codes are essential for accessing your account if you lose your phone or authenticator app, so treat them with the same care as your private keys. Write them down on paper and store them in a secure location. Many recommend keeping multiple copies in different safe places.
Avoid saving backup codes digitally in unsecured locations like your email, cloud storage, or phone notes. If you must store them digitally, use an encrypted password manager with a strong master password.
It's also a good idea to test your backup codes as soon as you receive them. Most platforms let you use a backup code in place of a 2FA code, so try one to confirm it works. This ensures you won’t face surprises if you need them later.
Keep in mind that backup codes are typically single-use only, meaning each code can be used just once. Track which codes you’ve used, and consider generating new ones periodically or after using several. Most platforms allow you to regenerate backup codes from your security settings, but doing so will invalidate any previously generated codes.
Best Practices for Managing Your 2FA
Once you've set up two-factor authentication (2FA), it's important to take steps to manage it effectively. Proper 2FA management not only safeguards your crypto accounts but also helps you avoid getting locked out due to common mistakes.
Storing Backup Codes Safely
Using a password manager is one of the safest ways to store your 2FA backup codes. Trusted options like 1Password, Bitwarden, and LastPass encrypt your data and sync it across devices. Within your password manager, create a secure note specifically for your backup codes. Clearly label each set with the platform name and the date they were generated - this is especially helpful when managing multiple accounts.
If you prefer offline storage, consider writing your backup codes on waterproof paper and keeping them in secure locations, such as a fireproof safe at home or a bank safety deposit box. Storing multiple copies in different places adds an extra layer of protection.
Avoid unsecured storage methods like saving codes in email drafts, cloud storage, or phone notes. These methods can expose your codes to unauthorized access. Also, whenever you use a backup code, generate a new set immediately, as the old ones become invalid.
Keeping your backup codes organized and secure ensures you're prepared for any unexpected challenges.
Managing Multiple 2FA Accounts
Authenticator apps now include features to help you manage multiple accounts. For instance, Google Authenticator offers cloud backup, while Authy syncs accounts across devices. Microsoft Authenticator goes a step further by allowing you to export TOTP seeds for recovery.
To streamline account management, rename each entry in your authenticator app with clear and recognizable labels, like "Crypto Exchange - Main." Avoid generic names like "Account 1" or random strings, as these can slow you down during critical moments.
Set up multiple recovery methods to bolster your security. In addition to backup codes, enable app backups and document your 2FA settings. Keep a secure record of which accounts have 2FA enabled, the authenticator app used, and the location of your backup codes. This preparation can save you time and frustration if you ever need to recover access.
Recovering Access if You Lose Your Device
Losing your 2FA device can be stressful, but proper backup management can make recovery smoother. Backup codes are your main tool for regaining access. Since these codes are typically single-use, prioritize logging into your most important accounts first. Once you're in, quickly set up 2FA on a new device to avoid exhausting your backup codes.
If you don't have your backup codes, contact customer support immediately. Be ready to provide account details, explain the issue clearly, and share proof of ownership, such as government-issued ID or transaction history for custodial wallets.
Some platforms simplify the recovery process. For example, CoinList offers a "Lost your 2FA?" option on its login page to help users regain access more efficiently. Avoid creating a new account on the same platform while you're locked out, as this can complicate the recovery process.
Be wary of scams during this vulnerable time. Legitimate platforms will never ask for upfront fees or request your seed phrase for recovery. Once you've regained access, immediately set up 2FA again with new backup codes. Store these codes securely using the methods mentioned earlier. This reinforces the importance of having multiple recovery options and keeping your backup codes accessible but secure.
sbb-itb-0796ce6
Using 2FA with Kryptonim
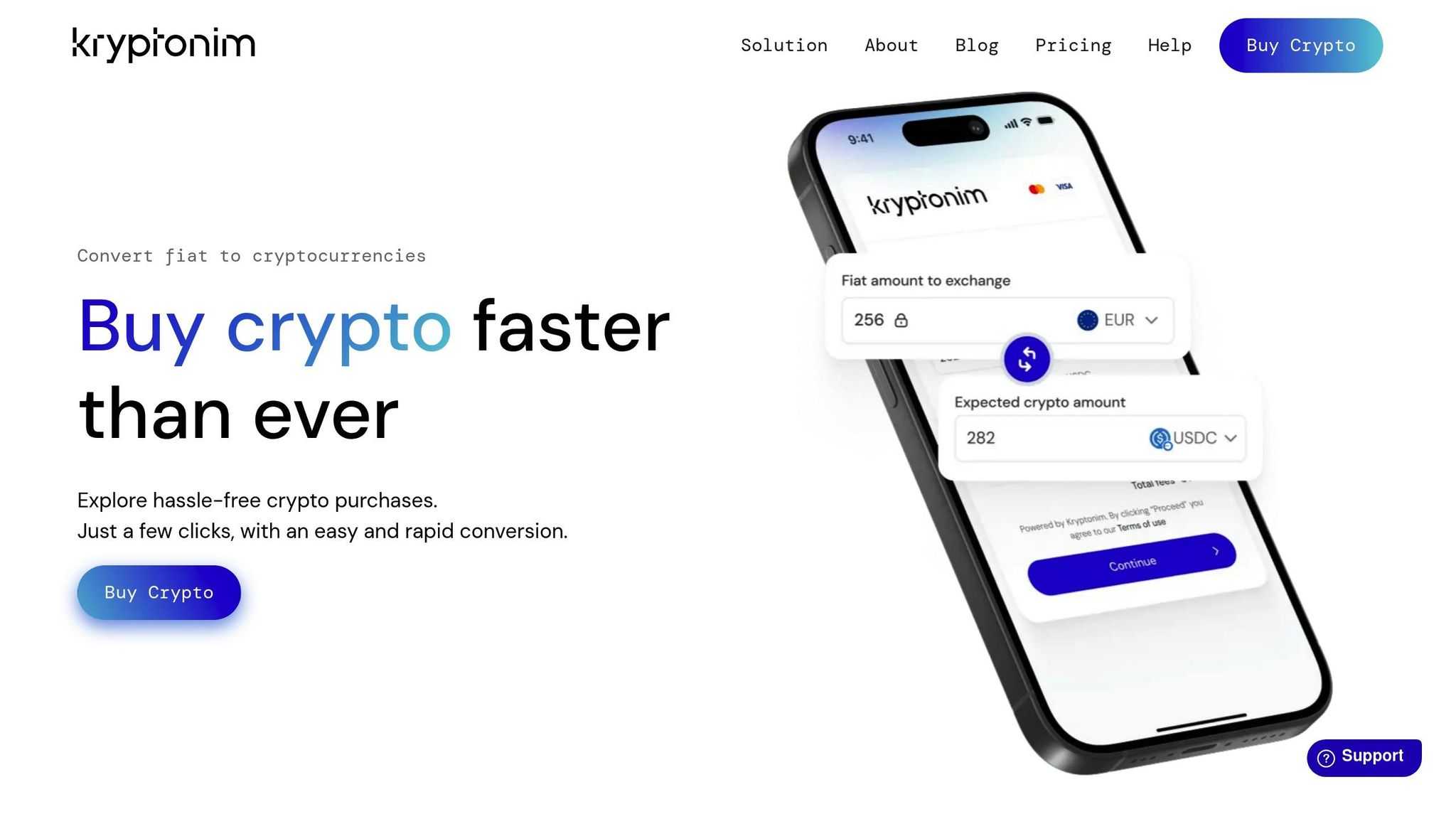
Let’s dive into how Kryptonim enhances your crypto security by integrating two-factor authentication (2FA) into its platform.
How Kryptonim Simplifies Crypto Transactions
Kryptonim operates as an EU-regulated platform, making crypto purchases quick and straightforward. Unlike many other services, it doesn’t require time-consuming sign-up processes, allowing you to focus on transactions without unnecessary delays.
Setting Up 2FA for Kryptonim Transactions
While Kryptonim ensures an easy user experience, safeguarding your wallet ultimately falls on you. Setting up 2FA is a critical step. Use an authenticator app like Google Authenticator, Authy, or Duo to generate time-sensitive one-time passwords. For added security, make sure to install the authenticator app on a separate device from the one you use for transactions. Also, create a strong, unique password for your wallet. Don’t forget about backup codes - store them securely as outlined earlier in this guide to ensure you’re prepared for any unexpected issues.
Benefits of 2FA on Kryptonim
Pairing Kryptonim’s user-friendly interface with robust 2FA practices creates a powerful shield against unauthorized transactions. Features like whitelisting withdrawal addresses and restricting access by IP address add extra layers of protection. Together, these measures help ensure your funds remain secure and inaccessible to unauthorized users.
Conclusion
Two-factor authentication (2FA) is your first line of defense against crypto theft and unauthorized access. This guide has outlined the essential steps to safeguard your digital assets with effective authentication methods.
Here’s the bottom line: authenticator apps strike the perfect balance between security and convenience, while SMS-based 2FA should be avoided when stronger options are available. Don’t forget to secure your backup codes - they’re critical to recovering access if needed. Platforms like Kryptonim make adopting these practices straightforward.
Kryptonim takes these security basics a step further by seamlessly integrating 2FA into its platform. As an EU-regulated service, it simplifies account creation without sacrificing security or transparency. With competitive rates and a user-friendly design, Kryptonim allows you to focus on securing your assets instead of wrestling with complicated processes.
Ultimately, your crypto security is in your hands. Pairing Kryptonim’s streamlined platform with robust 2FA practices sets you up for safer cryptocurrency management. Start by enabling 2FA on your main wallet today, and refine your security habits as you grow more confident.
While the crypto world keeps evolving, the principles of security remain constant. Strong passwords, dependable 2FA, and diligent backup practices will always be your best tools for protecting your investments, no matter which platforms or currencies you choose.
FAQs
What should I do if I lose the device with my 2FA authenticator app?
If you’ve lost the device with your 2FA authenticator app, don’t panic. Start by using the backup codes you received when setting up two-factor authentication. These codes are your safety net, designed to help you regain access to your account. Make sure you’ve stored them securely in a place only you can access.
Didn’t save your backup codes? Check if your authenticator app supports data restoration or account syncing. Many apps now offer cloud-based recovery options, which can be a lifesaver in situations like this.
If those options aren’t available, your next step is to reach out to the platform’s customer support team. Be prepared to verify your identity - this might involve confirming details through email, phone, or other methods. Taking these steps will help you regain access. Moving forward, always enable backups and store recovery information securely to protect your accounts.
What are the risks of using SMS-based 2FA for crypto transactions, and how can I stay protected?
SMS-based two-factor authentication (2FA) comes with some serious security concerns, including SIM swapping and message interception. In a SIM swap attack, cybercriminals manipulate mobile carriers into transferring your phone number to their own SIM card. This allows them to intercept your 2FA codes and gain access to sensitive accounts. Additionally, SMS messages can be intercepted, making this method far from foolproof.
For better protection, consider upgrading to more secure 2FA methods like authenticator apps or hardware security keys. These options are much harder to compromise through social engineering or interception, offering stronger safeguards for your crypto transactions.
Why is it important to store 2FA backup codes securely, and how can I do it safely?
Storing your 2FA backup codes securely is critical because they serve as your lifeline if you lose access to your main 2FA device. Without these codes, you might find yourself permanently locked out of your account.
The safest approach? Print the codes and store them in a secure physical location, like a fireproof safe or a safety deposit box. Avoid saving them digitally in places that could be vulnerable to hacking, such as cloud storage or unencrypted files. These steps can go a long way in protecting your accounts and ensuring you don’t lose access when you need it most.
