Double-Spending Risks: Problem and Solutions
Explore the risks of double-spending in cryptocurrency and discover how blockchain technology and user practices can enhance security.

Double-spending happens when someone fraudulently uses the same cryptocurrency more than once. This issue undermines the trust and value of digital currencies, as it can lead to financial losses, artificial inflation, and reduced confidence in blockchain systems.
Key points to know:
- Double-spending exploits delays in blockchain transaction confirmations.
- Attack methods include race attacks, Finney attacks, 51% attacks, and network manipulation.
- Blockchain prevents double-spending through public ledgers, cryptographic tools, and consensus mechanisms like Proof-of-Work (PoW) and Proof-of-Stake (PoS).
- Users can protect themselves by waiting for multiple confirmations, using regulated platforms, and monitoring transaction statuses.
Blockchain technology, combined with secure platforms and cautious user behavior, significantly reduces the risk of double-spending.
What Causes Double-Spending Attacks
Double-spending attacks highlight the importance of strong blockchain security measures. These attacks exploit vulnerabilities inherent to digital currencies and the decentralized nature of blockchain networks. Let’s dive into the factors that make such attacks possible and the methods attackers use to take advantage of these weaknesses.
Digital Currency Vulnerabilities
The digital format of cryptocurrencies makes them more susceptible to duplication compared to physical cash. Unlike a dollar bill, which can only be spent once, a digital coin can theoretically be copied and reused unless the system has safeguards in place to prevent it.
Network latency also plays a role. Transactions take time to propagate across nodes in a blockchain network. During this delay - ranging from seconds to minutes - different parts of the network may have conflicting views of which transactions are valid, creating opportunities for exploitation.
The mempool system, where unconfirmed transactions are stored, adds another layer of vulnerability. When the network is congested, transactions can sit in the mempool longer, extending the window of opportunity for attackers to attempt double-spending.
Common Attack Methods
Attackers have developed several strategies to exploit these vulnerabilities:
- Race attacks: This straightforward method involves broadcasting two conflicting transactions to different parts of the network simultaneously. The attacker aims to have one transaction accepted by a merchant while the other gets confirmed on the blockchain, effectively spending the same funds twice.
- Finney attacks: Named after cryptographer Hal Finney, this tactic involves pre-mining a transaction into a block without broadcasting it immediately. The attacker uses the same funds to make a purchase, and once the merchant accepts the payment, the pre-mined block is broadcasted, invalidating the merchant’s transaction.
- 51% attacks: These are the most severe. If an attacker gains control of more than half of the network’s mining power or validation nodes, they can rewrite transaction history, reverse confirmed transactions, and execute large-scale double-spending. While such attacks are resource-intensive on major networks like Bitcoin, they’ve been successful on smaller, less secure blockchains.
- Vector76 attacks: Combining elements of race and Finney attacks, this method targets merchants who accept transactions visible in the mempool but not yet confirmed in a block. The attacker exploits network topology by creating conflicting transactions and connecting to both the merchant’s node and a well-connected node.
Decentralized System Challenges
The decentralized nature of blockchain networks introduces unique challenges in combating double-spending. Without a central authority, the responsibility for verifying transactions falls on the network as a whole, which can lead to complications.
Network partitions - temporary splits in the network - can isolate groups of nodes. Each group may accept conflicting transactions, and when the network reconnects, one version must be discarded, potentially leaving some users with invalid transactions.
The order in which nodes receive transactions can also vary, and reaching consensus across thousands of nodes takes time. This delay creates opportunities for attackers to exploit inconsistencies in how the network views the blockchain’s current state.
Sybil attacks amplify these risks. By creating multiple fake identities, an attacker can control a significant portion of the network, manipulating how transactions are propagated and isolating specific nodes from accurate information.
Finally, economic incentives in decentralized systems can sometimes work against security. During network congestion, miners often prioritize transactions with higher fees. Attackers can exploit this by manipulating fees to increase the chances of their fraudulent transactions being processed. Additionally, temporary forks in the blockchain - caused by competing miners solving blocks simultaneously - naturally create opportunities for double-spending attempts.
These vulnerabilities and attack methods underscore the ongoing need for robust security measures to protect blockchain networks from double-spending threats.
How Blockchain Technology Prevents Double-Spending
Double-spending attacks take advantage of vulnerabilities to spend the same digital currency more than once. Blockchain technology, however, has built-in defenses that make these types of fraudulent activities extremely challenging to pull off. Here's how it works.
Public Ledgers and Cryptographic Safeguards
The public nature of blockchain ledgers is a powerful deterrent against double-spending. Every transaction is recorded on a transparent ledger visible to anyone in the network. If someone tries to spend the same currency twice, the conflicting transactions are immediately apparent to all participants.
Cryptographic hashing adds another layer of security by assigning a unique digital fingerprint to each block. Any attempt to alter a transaction - like trying to double-spend - would change the hash, instantly alerting the network to the tampering.
Additionally, digital signatures verify transaction ownership. These cryptographic proofs ensure that only the rightful owner of the funds can authorize a transaction, making it nearly impossible to forge or manipulate.
Together, these cryptographic tools create a secure foundation, which is further reinforced by consensus mechanisms.
Consensus Mechanisms for Transaction Validation
Blockchain networks rely on consensus mechanisms to validate transactions and maintain integrity.
- Proof-of-Work (PoW), used by Bitcoin, requires miners to solve complex mathematical puzzles to validate transactions and add new blocks. For an attacker to successfully double-spend, they’d need to control over 50% of the network’s computational power - a feat that’s prohibitively expensive and logistically daunting.
- Proof-of-Stake (PoS), on the other hand, selects validators based on the amount of cryptocurrency they hold and are willing to "stake." If a validator attempts to approve fraudulent transactions, they risk losing their staked funds, creating a strong financial disincentive for dishonest behavior.
In cases of conflict, the blockchain adheres to the longest chain rule, where the chain with the most work or stake is trusted.
Moreover, Byzantine Fault Tolerance (BFT) protocols ensure that the network remains secure even if some nodes act maliciously or fail. These systems allow the blockchain to function correctly as long as less than one-third of the nodes are compromised, providing resilience against coordinated attacks.
These mechanisms collectively ensure that transactions are validated securely and reliably.
Transaction Confirmations and Security Layers
The confirmation process strengthens transaction security over time. Each confirmation represents an additional block added to the chain after your transaction. The more confirmations a transaction has, the harder it becomes for an attacker to reverse it. For smaller transactions, fewer confirmations may suffice, while larger transactions often require six or more to ensure security.
Network monitoring tools play a crucial role in identifying and responding to double-spending attempts. If conflicting transactions are detected, these tools notify users and merchants, allowing them to act before finalizing a payment.
By adhering to the longest chain rule and requiring multiple confirmations, blockchains make validated transactions nearly irreversible.
Lastly, real-time transaction tracking provides users with transparency throughout the process. This allows individuals to monitor their payments as they progress through the network, offering peace of mind and early detection of any potential issues.
These layered defenses make blockchain technology a highly secure solution for preventing double-spending.
Platform Security Features Against Double-Spending
Cryptocurrency platforms go beyond blockchain's built-in defenses by adding extra layers of security. These measures work alongside consensus mechanisms and cryptographic protections to make double-spending even harder to pull off.
Key Security Measures
Modern platforms rely on continuous monitoring, thorough verification processes, and transparent transaction tracking to guard against double-spending. Continuous monitoring helps spot suspicious behavior before transactions are processed. Meanwhile, robust verification methods, which often include additional confirmation steps, quickly catch any inconsistencies. Together, these tools create a strong foundation for platforms like Kryptonim to deliver heightened security.
Kryptonim's Approach to Double-Spending Prevention
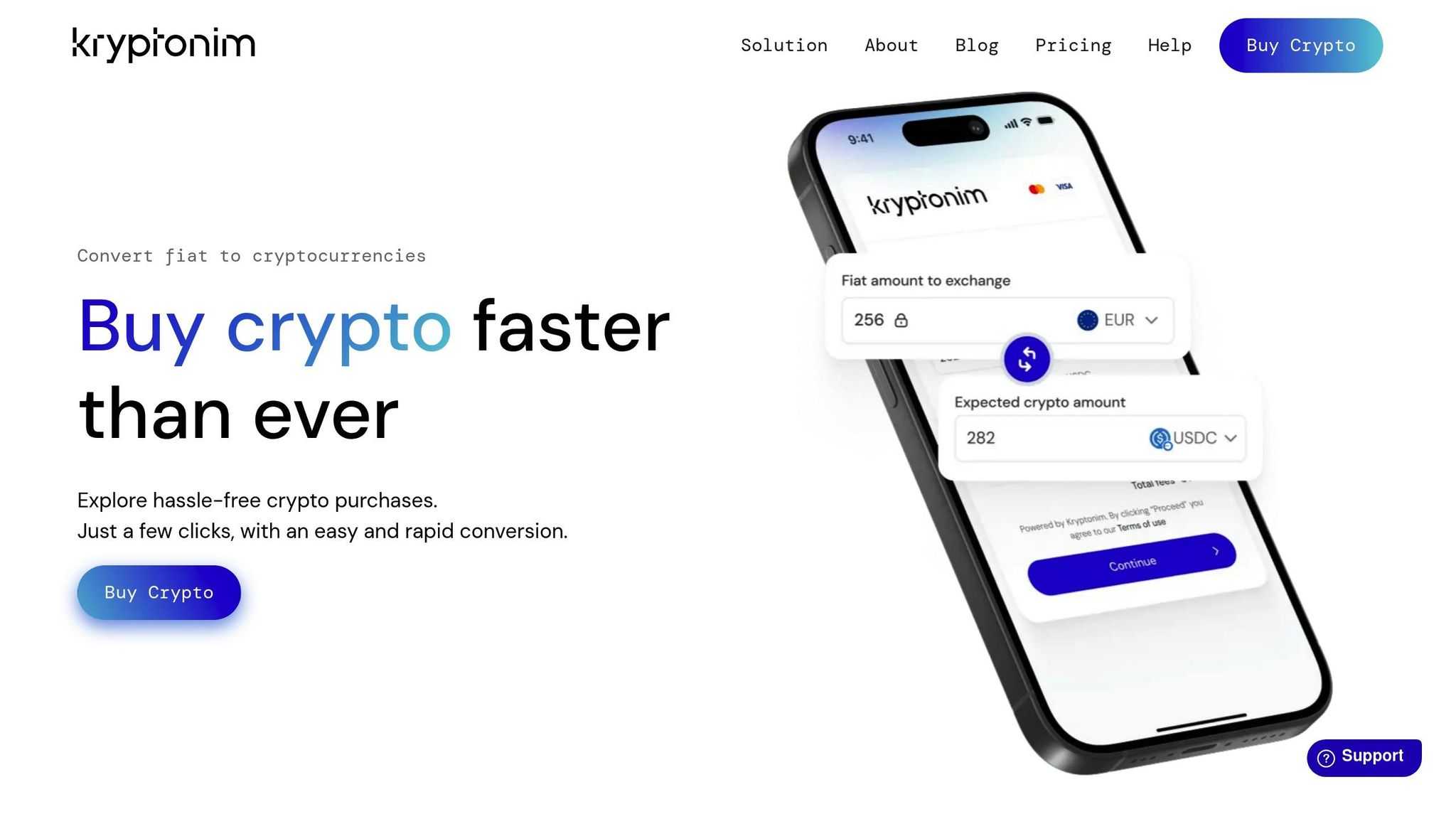
Kryptonim takes these security measures further by integrating its own proprietary checks, particularly for fiat-to-crypto transactions. Fully compliant with EU regulations, Kryptonim uses streamlined verification systems and maintains detailed transaction records to identify anomalies early. Features like transparent pricing and the ability to transact without creating an account help lower fraud risks. Additionally, their quick transaction processing reduces the time window for double-spending attempts, building user confidence and trust in the platform.
sbb-itb-0796ce6
How to Protect Yourself from Double-Spending
While blockchain technology and platform safeguards provide a strong foundation against double-spending, taking personal steps can further reduce your risks. By combining these proactive measures with existing protections, you can ensure your transactions are as secure as possible.
Wait for Multiple Transaction Confirmations
Transaction confirmations are key to securing your cryptocurrency transfers. Each confirmation adds a new block to the blockchain, making it harder for the transaction to be altered or reversed. For smaller payments - say, under $100 - one or two confirmations are usually enough. But for larger amounts, especially those over $1,000, it’s smart to wait for at least six confirmations before considering the transaction final. For example, Bitcoin transactions with six confirmations are widely regarded as irreversible, significantly reducing the risk of double-spending attacks.
Use Regulated and Secure Platforms
Choosing a trustworthy platform is another important layer of protection. Platforms operating under strict regulations, like those in the EU, follow rigorous compliance protocols, maintain detailed records, and use robust verification systems to enhance security. For instance, Kryptonim complies with EU regulations, ensuring high standards of transparency and security. Additionally, their no-account requirement limits the risks tied to storing personal credentials. Regulatory oversight like this helps prevent fraud and ensures platforms adhere to stringent safety measures.
Monitor Your Transaction Status
Keeping an eye on your transactions can help you catch issues early. Most blockchain networks provide a transaction ID (TXID) that allows you to track the progress of your payment in real time. Once you send cryptocurrency, locate the transaction hash in your wallet or platform interface and verify it on a blockchain explorer. If the TXID doesn’t update within a few minutes, it’s a good idea to contact support.
Be aware that network congestion can cause delays, leading to higher fees and longer confirmation times. Understanding these patterns can help you differentiate between normal delays and potential security issues. Many wallets and platforms offer alerts to notify you when confirmations occur, so you don’t have to check manually. However, if you notice unusual signs - like a transaction disappearing from the mempool, unexpected status changes, or conflicting notifications - contact your platform's support team immediately. Avoid making additional transactions until the issue is resolved to prevent further complications.
Conclusion: Building Trust in Blockchain Networks
Double-spending attacks pose a real threat to digital currencies, but a combination of layered blockchain defenses, secure platforms, and informed users helps mitigate these risks. Today, coordinated technical and regulatory measures work together to address vulnerabilities, creating a robust system that integrates technical safeguards with user awareness.
Blockchain's technical defenses are rooted in its very design, aiming to prevent fraud at every level. Public ledgers ensure that every transaction is transparent and verifiable, while consensus mechanisms like Proof of Work and Proof of Stake make altering transaction records prohibitively expensive for attackers. These features provide the backbone of trust in decentralized networks.
In addition to blockchain's built-in security, platforms add another layer of protection. For example, EU-regulated platforms like Kryptonim implement strict compliance and verification protocols to strengthen blockchain defenses. However, technology and regulation alone can’t do the job - users play a crucial role in securing the network. Simple actions like waiting for multiple transaction confirmations, using regulated platforms, and keeping an eye on transaction statuses can significantly reduce risks. When users understand how to verify transactions and spot warning signs, they actively contribute to the network's overall security.
At its core, blockchain security is a shared responsibility. Miners and users work together to maintain transaction integrity, building trust as technology evolves and regulations improve. Blockchain isn't just about creating digital currencies - it’s about establishing secure, transparent systems that empower people to transact with confidence.
FAQs
Why is waiting for multiple confirmations important for preventing double-spending in cryptocurrency?
When it comes to blockchain transactions, waiting for multiple confirmations isn’t just a formality - it’s a key step in ensuring security. Each confirmation means the transaction has been added to a new block, making it increasingly harder for anyone to tamper with or reverse.
Every extra confirmation adds another layer of protection, significantly reducing the chances of double-spending. This process safeguards the transaction’s integrity and shields against any attempts to misuse the same cryptocurrency more than once.
How do platforms like Kryptonim protect against double-spending attacks?
To combat double-spending attacks, platforms such as Kryptonim rely on a combination of robust security measures. These include requiring multiple confirmations for transactions to verify their authenticity, employing decentralized consensus mechanisms to uphold the network's integrity, and utilizing advanced encryption alongside cryptographic methods to protect sensitive data.
By combining these approaches, platforms ensure transactions are both final and resistant to tampering. This makes double-spending nearly impossible, offering users a trusted and secure environment for their activities.
Why are smaller blockchain networks at greater risk of 51% attacks than larger ones like Bitcoin?
Smaller blockchain networks face a higher risk of 51% attacks due to their relatively lower computational power, often referred to as hashing power. With less processing power securing the network, it becomes both easier and cheaper for an attacker to gain the majority control needed to compromise the system.
When someone seizes control of more than 50% of the network's power, they can manipulate transactions in harmful ways. For example, they could reverse payments or enable double-spending, actions that severely damage trust in the blockchain. On the other hand, larger networks like Bitcoin are far less vulnerable. Their massive hashing power makes such attacks not only financially prohibitive but also nearly impossible to execute from a logistical standpoint.
